Posts tagged reverse engineering
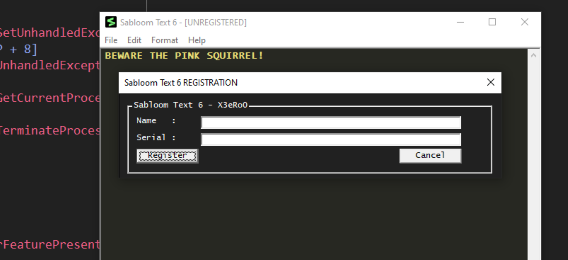
Today we look at another crackme, SabloomText_v6!
The difficulty is rated at level 4.8 of 6 - I think perhaps it was more like a 4.
I am not going to say anything about it in this section as it would spoil a cool surprise if you want to try it yourself!
Here is the link if you want to try it Sabloom Text 6
Tools used today are x64dbg, PEStudio, F# and C++
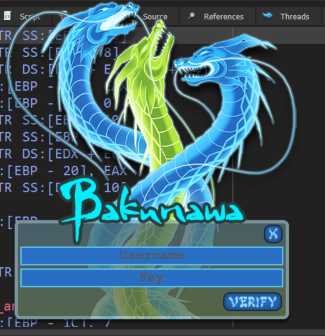
In this post we’ll look at another crackme, Bakunawa!
This one was listed as level 5 (Very Hard) and certainly was not without its difficulties!
Featuring a sort-of virtual machine executing real x86 instructions encoded into an odd binary file as a point of obsfucation, this took me quite a long time to figure out. I built some tools in the process and finally a Keygen program once the algorithm was identified and reversed.
Major spoilers follow, here’s the link if you want to have a go yourself!
Tools used today are x64dbg, PEStudio, IDA Pro, F# and C++
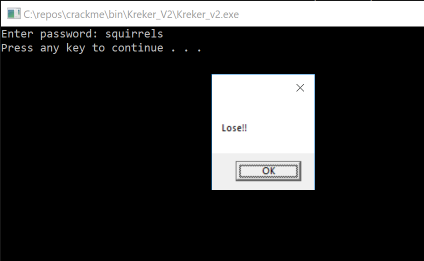
In this article we’ll look at another crackme. This one was pretty difficult and has a bunch of cool stuff in it, including the injection and execution of obfsucated code into another process.
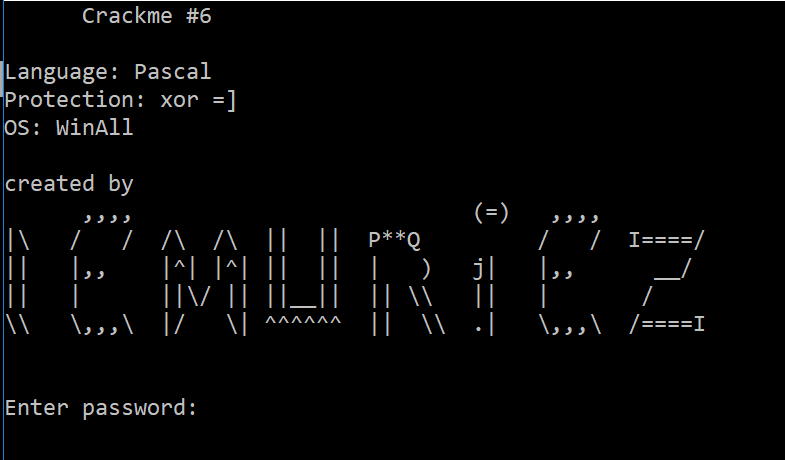
In a previous article I described the process of reverse-engineering a crackme. These are programs designed to be broken with various counter-mesaures and challenges. As a break from my hardware work, I thought I would have a go at another one.
As an entertaining start to the new year, this post will cover the basics of reverse engineering a program and breaking its password protection. Of course, I do not advocate software piracy in any way, and the program in question is called a crackme which is a program designed to broken, with various measures to make it harder for you. They come in different levels of difficulty, the one under the microsope today is a relatively easy one - however, breaking even the simplest program requires a fairly deep understanding of computers, and the process might be quite interesting if you don’t know how it’s done. Let’s have a look at it: